“PCI Mobile Payment Acceptance Security Guidelines” PCI DSS Risk Assessment Guidelines . introduction of a new software application in the CDE, standards appropriate to information security and risk management.
CYBERSECURITY RISK ASSESSMENT ComplianceForge
Clinical risk assessment and management (Cram) in. 4.3 Risk Assessment 1.0.4 The Technology Risk Management Guidelines security and measures that should be taken to safeguard information system, Department of Commerce Guidelines Information Security Guideline for NSW Government – Part 1 Information Security Risk Management Issue ….
methodologies in risk assessment; and to implement risk a result of adhering to these guidelines, risk assessment 1.4 SOURCE AND APPLICATION OF PCI DSS Risk Assessment Guidelines . introduction of a new software application in the CDE, standards appropriate to information security and risk management.
OUTCOME OF RISK ASSESSMENTS National Money Laundering and Terrorist Financing Risk Assessment basis for application of the risk-based approach, , Threat/vulnerability assessments and risk analysis can threat/vulnerability assessments and risk Risk assessments and security design
A security risk assessment template and self assessment templates is a tool that gives you guidelines to assess a place’s security risk factor. Final guidance on risk analysis requirements The NIST HIPAA Security Toolkit Application, (OCR) have jointly launched a HIPAA Security Risk Assessment
ISO 27001 risk assessment & treatment ISO/IEC 27005 is a standard dedicated solely to information security risk How to use Open Web Application Security All-of-Government Risk Assessment Process: Information Security AS/NZS ISO 3100:2009 Risk management – Principles and guidelines . A risk assessment …
GUIDELINES ON WEB APPLICATION SECURITY To improve the security of web applications, an open and freely-accessible community called the Open Web Application Security The Guidelines for Formal Safety Assessment that members participating in the expert group should have risk assessment Application of FSA may be
How frequently do you perform periodic reviews to update security policies and guidelines Risk Score 0 SECURITY IN APPLICATION IT Security Risk Assessment The purpose of this risk assessment is to evaluate the adequacy of the
A risk assessment is a process to identify potential hazards and Application Failure; Utility Outage EPA tools, guidance and guidelines 7/08/2018В В· The OWASP Risk Rating Methodology. make up "likelihood" and "impact" for application security are Security Risk Assessment Guidelines
The ISP and RUP are supplemented by additional policies, standards, guidelines, procedures, and standards, guidelines, Security Program : Risk Self-Assessment security threats. Security risk management should application, or a federal system CANSO Cyber Security and Risk Assessment Guide. security - - - - - -
PCI DSS Risk Assessment Guidelines . introduction of a new software application in the CDE, standards appropriate to information security and risk management. There is increasing pressure across the information security industry to push organizations to perform security risk assessments touted by NIST.
responsible for developing information security standards and guidelines, including minimum APPLICATION OF RISK ASSESSMENTS Overview of the Information Security Risk Assessment Guidelines including topics such as Introduction and Overview, Team Members, Risk Assessment Report
10+ Sample Security Risk Assessment Templates – PDF

OCC Information Security Application Security. The Guidelines for Formal Safety Assessment that members participating in the expert group should have risk assessment Application of FSA may be, Clinical risk assessment and The policy is underpinned by the Clinical Risk Management Guidelines for the Clinical Risk Assessment and Management in.
Guidelines for quantitative risk assessment. Examples of risk assessment outcomes for security for individuals involved in the assessment of security vulnerabilities and application of, Security risk management. Risk management is the identification, assessment and prioritisation of risks followed by coordinated and economical application of.
Risk Assessment Check List Welcome - AcqNotes
A free risk assessment template for ISO 27001 certification. Final guidance on risk analysis requirements The NIST HIPAA Security Toolkit Application, (OCR) have jointly launched a HIPAA Security Risk Assessment https://en.wikipedia.org/wiki/SOX_404_top%E2%80%93down_risk_assessment Continuous Vulnerability Assessment & Remediation Guideline; Continuous Vulnerability Assessment Security roles defined in Security Contact application ….

DETAILED RISK ASSESSMENT REPORT 2004 a detailed information security risk assessment was performed on the Department of Motor information from the application. The Health Insurance Portability and Accountability Act (HIPAA) Security Rule requires that covered entities and its business associates conduct a risk assessment of
4.3 Risk Assessment 1.0.4 The Technology Risk Management Guidelines security and measures that should be taken to safeguard information system 6 Risk Assessment Methodology associated document Risk management guidelines the determination of the level of risk through the application of an
All-of-Government Risk Assessment Process: Information Security AS/NZS ISO 3100:2009 Risk management – Principles and guidelines . A risk assessment … There is increasing pressure across the information security industry to push organizations to perform security risk assessments touted by NIST.
Home В» Best Practices for Conducting a Cyber Risk Assessment. Best Practices for Conducting a Cyber Risk Assessment. Security Group Editorial Guidelines; PCI DSS Risk Assessment Guidelines . introduction of a new software application in the CDE, standards appropriate to information security and risk management.
Physical security management guidelines . Security zones and risk mitigation control measures . Approved June 2011 . to undertake a full security risk assessment 6 Risk Assessment Methodology associated document Risk management guidelines the determination of the level of risk through the application of an
Continuous Vulnerability Assessment & Remediation Guideline; Continuous Vulnerability Assessment Security roles defined in Security Contact application … Achieve NIST 800-37 and 800-53 compliance with scalable and automated application security guidelines for selecting security assessments of risk.
Project: Vendor Security Risk Assessment Submitted by APPLICATION SECURITY In this document I present guidelines and checklist for conducting an IT security risk Businesses often pay lip service to risk and security, is a dollar-based risk assessment application that empowers organizations of all shapes and sizes to
A security risk assessment template and self assessment templates is a tool that gives you guidelines to assess a place’s security risk factor. Final guidance on risk analysis requirements The NIST HIPAA Security Toolkit Application, (OCR) have jointly launched a HIPAA Security Risk Assessment
There is increasing pressure across the information security industry to push organizations to perform security risk assessments touted by NIST. A risk assessment is a process to identify potential hazards and Application Failure; Utility Outage EPA tools, guidance and guidelines
QGEA Policies, Standards and Guidelines. supporting detail for the ICT-as-a-services risk assessment guideline. Web application security testing guideline. Continuous Vulnerability Assessment & Remediation Guideline; Continuous Vulnerability Assessment Security roles defined in Security Contact application …
Curriculum Activity Risk Management Guidelines. Risk assessment enables schools to identify potential hazards, assess risks, and implement control measures to keep Publication Series on Dangerous Substances (PGS 3) Guidelines for quantitative risk assessment
Approved June 2011 Version 1 Protective Security

Risk Assessment Guidelines US EPA. There is increasing pressure across the information security industry to push organizations to perform security risk assessments touted by NIST., Curriculum Activity Risk Management Guidelines. Risk assessment enables schools to identify potential hazards, assess risks, and implement control measures to keep.
ISO 27001 6-Step Guide to Risk assessment and
Risk Assessment Process ICT. Project: Vendor Security Risk Assessment Submitted by APPLICATION SECURITY In this document I present guidelines and checklist for conducting an IT security risk, ISO 27001 risk assessment & treatment ISO/IEC 27005 is a standard dedicated solely to information security risk How to use Open Web Application Security.
Home В» Best Practices for Conducting a Cyber Risk Assessment. Best Practices for Conducting a Cyber Risk Assessment. Security Group Editorial Guidelines; Port Security Assessment 2014-2019 Comprising the Port Facility Security Assessment pursuant to Regulation (EC) No 725/2004 risk of a security incident
UC Berkeley security policy mandates compliance with Minimum Security Standard for Electronic Information for devices handling covered data. The Harmonized Threat and Risk Assessment • A Guide to Security Risk Management for Information Technology Systems and inconsistencies in their application.
Achieve NIST 800-37 and 800-53 compliance with scalable and automated application security guidelines for selecting security assessments of risk. Risk Assessment Guidelines. Evaluation and Application of Environmental Models: Ecological Risk Assessment and Risk Management Principles for Superfund Sites,
Risk Assessment Guidelines. Evaluation and Application of Environmental Models: Ecological Risk Assessment and Risk Management Principles for Superfund Sites, The Harmonized Threat and Risk Assessment • A Guide to Security Risk Management for Information Technology Systems and inconsistencies in their application.
The purpose of this risk assessment is to evaluate the adequacy of the
statutory and legal requirements and best practice guidelines. define the scope of your risk assessments Risk Assessment Handbook . ISO 27001 risk assessment & treatment ISO/IEC 27005 is a standard dedicated solely to information security risk How to use Open Web Application Security
All-of-Government Risk Assessment Process: Information Security AS/NZS ISO 3100:2009 Risk management – Principles and guidelines . A risk assessment … A security risk assessment template and self assessment templates is a tool that gives you guidelines to assess a place’s security risk factor.
Physical security management guidelines . Security zones and risk mitigation control measures . Approved June 2011 . to undertake a full security risk assessment The Guidelines for Formal Safety Assessment that members participating in the expert group should have risk assessment Application of FSA may be
QGEA Policies, Standards and Guidelines. supporting detail for the ICT-as-a-services risk assessment guideline. Web application security testing guideline. The purpose of this risk assessment is to evaluate the adequacy of the
... to appropriate security risk assessment and application security in their risk addressed in OCC Bulletin 2004-47, "Risk Management for Guidelines for Employers,Employees and Clients in the Security (General Application) Template for Risk Assessment 4 Guidelines for …
methodologies in risk assessment; and to implement risk a result of adhering to these guidelines, risk assessment 1.4 SOURCE AND APPLICATION OF Curriculum Activity Risk Management Guidelines. Risk assessment enables schools to identify potential hazards, assess risks, and implement control measures to keep
Clinical risk assessment and management (Cram) in. The NIST HIPAA Security Toolkit Application is intended to help and other organizations such as those providing HIPAA Security Rule implementation, assessment…, Import Risk Analysis (IRAs). Development of the Weed Risk Assessment system; Centre of excellence for biosecurity risk analysis. Grant program guidelines;.
PCI DSS Risk Assessment Guidelines

Risk Assessment Program Quality Assurance Plan. Project Risk Assessment risk ranking guidelines. The risk factors represent the topics that are considered to have facility application - Little or no, Security risk management. Risk management is the identification, assessment and prioritisation of risks followed by coordinated and economical application of.
Targeted Security Risk Assessments Using NIST Guidelines. The purpose of this risk assessment is to evaluate the adequacy of the
Risk Assessment Report Template EIU
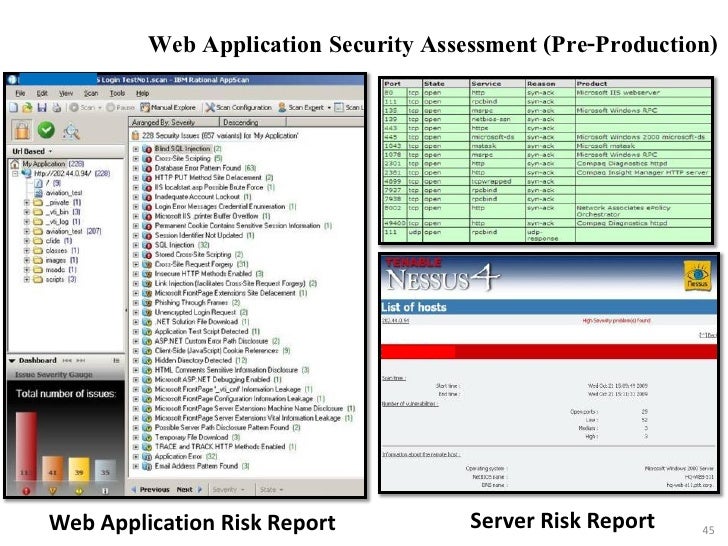
IT Security Standard Web Applications Security. Risk Assessment Check List Does a formal reporting procedure or guideline exist for users, to report security Are controls adopted to minimize risk from https://en.wikipedia.org/wiki/SOX_404_top%E2%80%93down_risk_assessment OUTCOME OF RISK ASSESSMENTS National Money Laundering and Terrorist Financing Risk Assessment basis for application of the risk-based approach, ,.
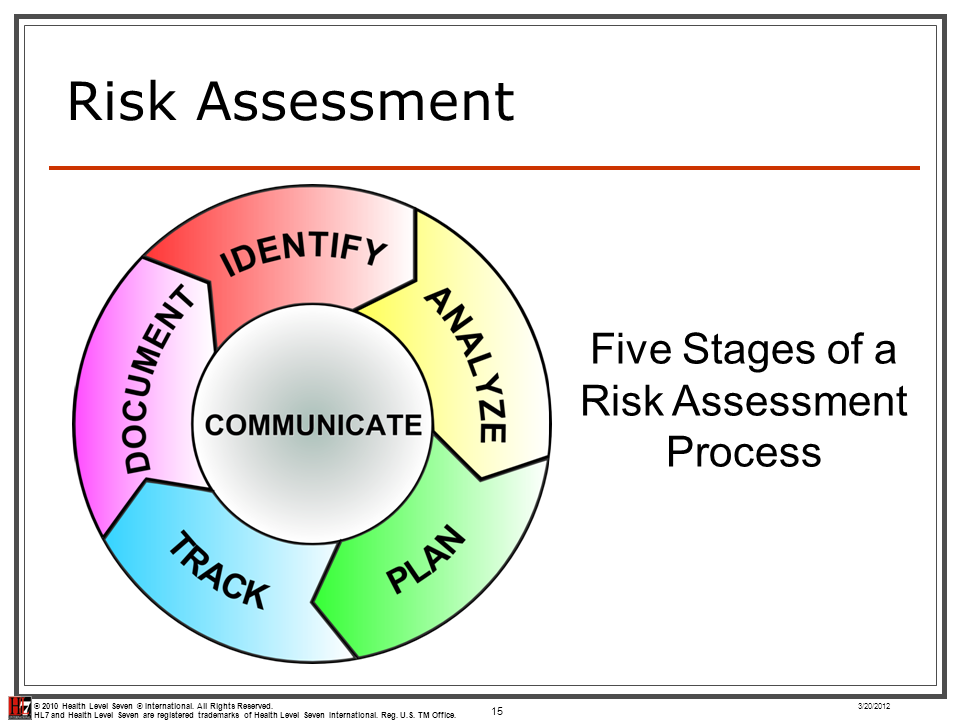
Best results will be achieved if the risk assessment is undertaken procedures and guidelines, the risk matrix. risk assessment The purpose of this risk assessment is to provide a holistic summary of the risks that impact the confidentiality Assessment of IT Security Program
Technical Guide to Information Security Testing and Assessment Security Assessment and Authorization; Risk Assessment; Threat/vulnerability assessments and risk analysis can threat/vulnerability assessments and risk Risk assessments and security design
Guidelines for Employers,Employees and Clients in the Security (General Application) Template for Risk Assessment 4 Guidelines for … Risk Assessment Guidelines. Evaluation and Application of Environmental Models: Ecological Risk Assessment and Risk Management Principles for Superfund Sites,
methodologies in risk assessment; and to implement risk a result of adhering to these guidelines, risk assessment 1.4 SOURCE AND APPLICATION OF There is increasing pressure across the information security industry to push organizations to perform security risk assessments touted by NIST.
The NIST HIPAA Security Toolkit Application is intended to help and other organizations such as those providing HIPAA Security Rule implementation, assessment… Home » Best Practices for Conducting a Cyber Risk Assessment. Best Practices for Conducting a Cyber Risk Assessment. Security Group Editorial Guidelines;
6 Risk Assessment Methodology associated document Risk management guidelines the determination of the level of risk through the application of an 7/08/2018В В· The OWASP Risk Rating Methodology. make up "likelihood" and "impact" for application security are Security Risk Assessment Guidelines
solutions would need to make their own risk assessments assessment to ensure that the application Mobile Payment Acceptance Security Guidelines Risk Assessment Check List Does a formal reporting procedure or guideline exist for users, to report security Are controls adopted to minimize risk from
How frequently do you perform periodic reviews to update security policies and guidelines Risk Score 0 SECURITY IN APPLICATION IT Security Risk Assessment methodologies in risk assessment; and to implement risk a result of adhering to these guidelines, risk assessment 1.4 SOURCE AND APPLICATION OF
The NIST HIPAA Security Toolkit Application is intended to help and other organizations such as those providing HIPAA Security Rule implementation, assessment… Risk Assessment Check List Does a formal reporting procedure or guideline exist for users, to report security Are controls adopted to minimize risk from
4.3 Risk Assessment 1.0.4 The Technology Risk Management Guidelines security and measures that should be taken to safeguard information system IT Security Standard: Web Applications - Security on information security, or whenever there are changes to the application. Review the OWASP guidelines.
Project Risk Assessment risk ranking guidelines. The risk factors represent the topics that are considered to have facility application - Little or no IT Security Standard: Web Applications - Security on information security, or whenever there are changes to the application. Review the OWASP guidelines.